Backlog Crisis at the National Vulnerability Database

Backlog Crisis at the National Vulnerability Database
The NVD is struggling with a backlog of thousands of unprocessed CVEs, impacting CPE to CVE mappings, and leaving defenders in the dark on the vulnerability risk potential of their assets.
Quick Talking Points
What is the current status of processing CVEs at the NVD?
The NVD is facing a substantial backlog, with over 2,150 unaddressed CVEs, representing more than 90% of all CVEs published since February 15th.
How is the NVD addressing the backlog of unprocessed vulnerabilities?
The NVD has acknowledged the issue and is working to establish a consortium to develop improved tools and methods. However, this may lead to temporary delays in analysis efforts.
What percentage of published CVEs have been associated with a Common Platform Enumeration (CPE) in the NVD database since February 12, 2024?
Only about 8% of published CVEs have been associated with a CPE in the NVD database, raising concerns for stakeholders relying solely on the NVD for critical information.
What interim solutions are available to mitigate the impact of delays in processing vulnerabilities at the NVD?
The Community edition of Defused offers a free solution to detect exploits against public-facing infrastructure, providing an additional layer of security during this period of uncertainty.
Backlog Crisis at the National Vulnerability Database
The NIST NVD equips defenders with a suite of automated tools for robust vulnerability management, offering a comprehensive security checklist, detailed software flaw reports, and extensive product information, all underpinned by precise impact metrics. Often, the NVD is the foundational element in the cybersecurity ‘security jenga tower,’ with a multitude of tools, processes, and systems depending on its reliable vulnerability databases.
Regrettably, the NVD is currently wrestling with significant delays in processing CVE vulnerabilities, which are pivotal to cyber security defense strategies. A concerning backlog of approximately 2,500 CVEs *, which constitutes around 40% of all CVEs disclosed this year, has yet to be addressed. The situation deteriorated after February 15th, when the NVD posted a notice about these delays, and since then, only 59 CVEs have been processed, resulting in an overwhelming backlog of over 2,150 CVEs—more than 90% of the total published in that period.
An analysis of the data from February 12, 2024, shows that a mere 8% of the CVEs published have been linked with a CPE in the NVD’s vulnerability db. This significant discrepancy in CPE to CVE search mappings raises alarms for those who rely on the NIST CVE database for essential information, potentially causing them to miss a multitude of emerging vulnerabilities.
In a detailed blog post *, vulnerability researcher Jay Jacobs explored the changing dynamics of CVE NVD enrichment at the NIST National Vulnerability Database. Jacobs used striking visuals to compare the current year’s data with the previous year’s, highlighting a discernible shift in the vulnerability disclosure process.
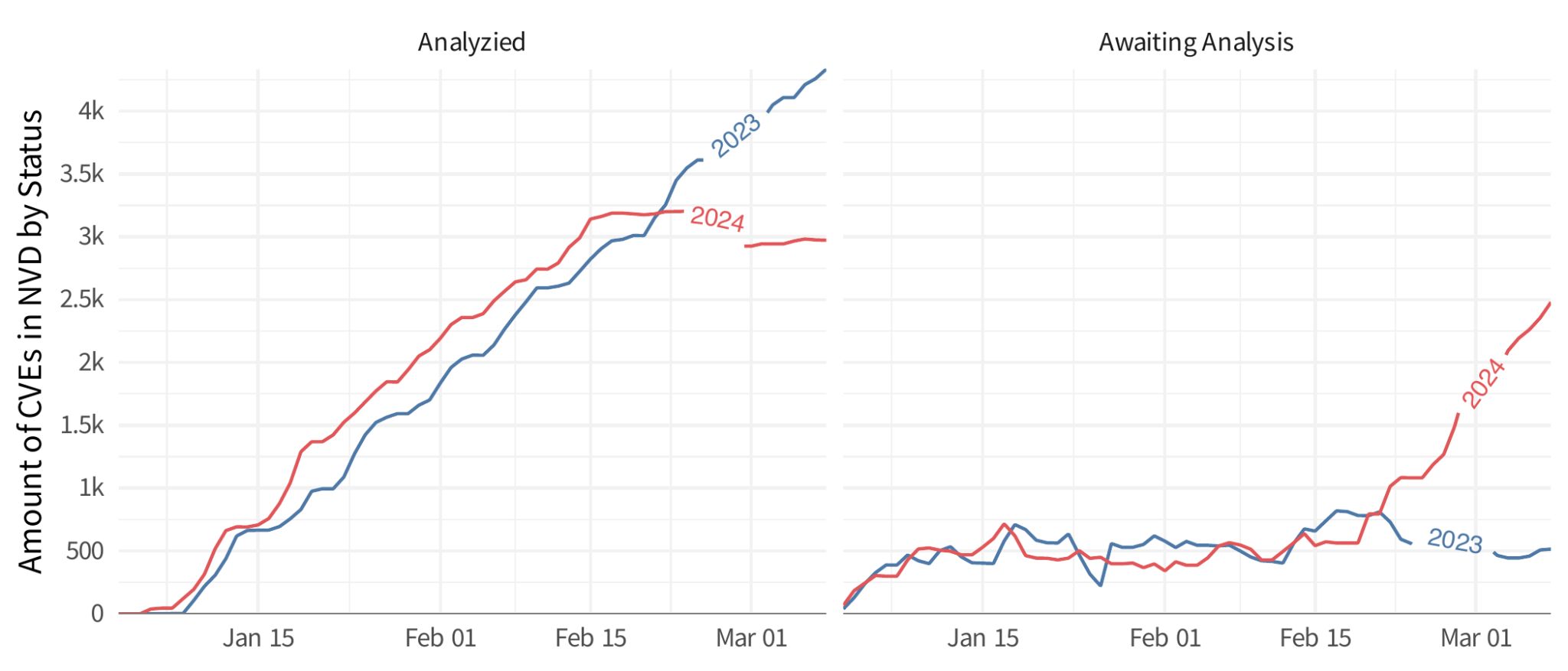 Jacobs specifically noted a downturn in the completion rate of the ‘Analyzed’ status for CVEs around February 15th, which coincided with the NVD’s announcement of a new consortium. He also pointed out a lag in updating essential vulnerability metrics, such as CVSS v3 and CVSS v2 scores, along with Common Weakness Enumeration (CWE) identifiers, although some CVEs continued to receive these critical updates.
Jacobs specifically noted a downturn in the completion rate of the ‘Analyzed’ status for CVEs around February 15th, which coincided with the NVD’s announcement of a new consortium. He also pointed out a lag in updating essential vulnerability metrics, such as CVSS v3 and CVSS v2 scores, along with Common Weakness Enumeration (CWE) identifiers, although some CVEs continued to receive these critical updates.
Despite the backlog, the NIST NVD seems to be strategically focusing on selective enrichment of high-impact vulnerabilities, such as CVE-2024-27198. This CVE has been thoroughly enriched and included in the CISA Known Exploited Vulnerabilities Catalog, demonstrating the NVD’s commitment to prioritizing threats that present the most significant risks.
The outlook for the NIST NVD’s processing capabilities is currently uncertain, with no definitive schedule for addressing the backlog. Nevertheless, the NVD has recognized the problem and is actively pursuing solutions. They have announced an initiative to form a consortium aimed at boosting the efficiency and effectiveness of the NVD program. However, this move signals a transitional phase that may temporarily hinder analysis efforts.
In the meantime, tools like the Community edition of the Defused product are at your disposal to help lessen the impact of these delays. This community edition provides a complimentary solution to identify exploits targeting public-facing infrastructure, adding an additional layer of security in times of uncertainty.
The backlog at the NVD transcends mere inconvenience; it represents a significant gap in our collective cybersecurity defense. As the NVD strives for a more fortified and streamlined system, it’s imperative that the cybersecurity community unites to devise interim solutions and remain vigilant against emerging threats. The path forward is fraught with challenges, yet through collaborative efforts and pioneering strategies, we can steer through this predicament and emerge more resilient.