Cyber Deception VS Honeypots

“Deception… it’s like honeypots?” is probably the most common commentary we hear when discussing deception with people.
The comment points us in the right direction. Honeypots are certainly a tool for doing cyber deception, but merely that - one tool among many. A useful analogy here might be that a honeypot is to cyber deception what a hammer is to construction work. The former is a tool to achieve progress in the other, the latter is a whole practice that involves multiple tools & processes.
Defining Cyber Deception
The purpose of using cyber deception, or any type of deception for that matter, is “deliberately inducing erroneous sensemaking to gain an advantage.” This is an broad definition, and if you think of it, you have very likely used deception in mundane life events on multiple occasions. Keeping a party secret to surprise someone on their birthday, or maintaining the myth of Santa Claus to enhance a child’s Christmas experience are such examples. (Sorry if we spoiled it for you!)
The applications of cyber deception are equally diverse. In most situations, the use case for cyber deception involves boosting general cyber resilience, but of course even this is just a subset of all the possible use cases of deception in the cyber domain.
Noun
Two Examples
To return to the introductionary paragraph, honeypots are but a single tool in a wide array of possible deceptive measures. Using our definition of deception in parallel with a use case for a honeypot would look as follows:
A honeypot may be installed (deliberately) to appear as a lucrative hacking target for cyber attackers (inducing erroneous sensemaking) and alerting may be built into it to receive a signal of compromise - in optimal cases, without the attacker knowing they’ve been discovered (gaining an advantage).
However, we can swap out the scenario to anything of our pleasing. A data-related deception scenario might look like this:
A fileshare with interesting-looking but fake files is linked to a computer (deliberately), with the files made to appear as internal documents (inducing erronenous sensemaking), to track, alert and gain intelligence against internal or external parties looking to steal company data (gain an advantage).
Now, if you observe the MITRE ATT&CK matrix for all possible tactics & techniques available for attackers, you can really let your imagination roll with all possible deception scenarios that could be built against various attacks!

Decoys vs Honeypots
Honeypots and decoys are also often used interchangeably, and these two concepts are much more closer to each other. The main difference is that honeypots are predominantly thought of being network-accessible fake services or assets, like fake SSH servers - or even full-blown Windows machines (commonly used for research purposes) - whereas decoys can manifest themselves in other ways, for example as fake network traffic that is replayed over a network to entice attackers to act on it. With this in mind, a network decoy and a honeypot are fairly interchangeable terms.
Honeypots, then, are a subcategory of decoys. The semantics are not, however, written into stone and different people and vendors will use different words to describe separate decoy capabilities (lures, breadcrumbs, and other terminology have been observed to describe various types of credential decoys, for example.)
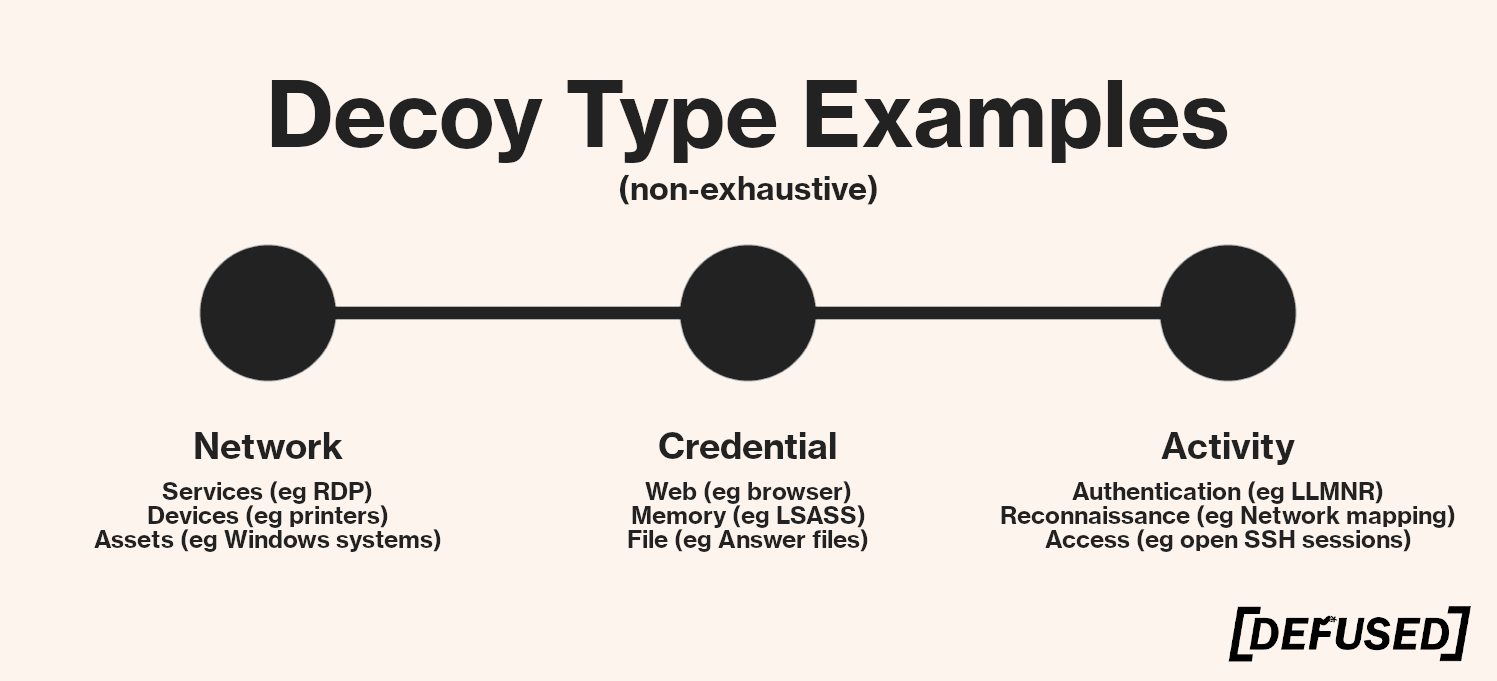
At Defused we use the decoy term with a suitable prefix, as we believe it draws a more accurate picture of what the purpose of a given decoy element is. It is difficult, for instance, to instantly know what a lure is in the cyber domain, but replacing that with a term like credential decoy makes the capability much clearer (in our opinion).
Deploying Deception vs Honeypots
The opportunities to practice deception may seem limitless, but for effective cyber defense purposes some easy low-hanging fruits exist. For internal networks, lateral movement still remains a key activity and thus network decoys, or honeypots, offer great value. Multiple open-source implementations have been built over the years. The big difference between a deception platform and an open-source honeypot usually is that platforms help you handle deployment, alerting and integration, as well as maintenace, whereas open source implementations may leave it mostly for the user to handle.
On the other hand, open source honeypots (and other decoy types) may exist which provide a capability that no commercial vendor has. The defender should weigh what the use case is that they wish to build the deception on top of, and judge what is the most suitable decoy type available for their disposal.
Wrapping Up
Cyber deception offers powerful capabilities to gain advantages, but this requires a good set of creativity and the right kind of tooling that suits the purposes of the user. Honeypots are still a powerful tool to do so in certain circumstances (mostly network-traffic related scenarios), but should absolutely not be the only tool in the repertoire for the modern cyber defense environment.
Defused is launching a new free tier for VMWare environments, offering easy deployment of our various decoy capabilities. Sign up for our free plan today here and get instantly notified on launch.