Vulnerabilities Long Tail

Vulnerabilities Long Tail
In 2023 almost thirty thousand vulnerabilities were disclosed, up from about approximately twenty five thousand in 2022. While the increase is noticeable, less than 1% contributed to the highest risk. While only a smaller subset may be relevant to a given organization, it’s still quite an effort to keep up with and ensure that all your systems are properly configured and patched.
The constant stream of new vulnerabilities keep InfoSec professionals busy, but there is also a significant long tail of older vulnerabilities that is just as important. After all, to an attacker, it does not matter how old a given vulnerability is, as long as it can be reliably exploited.
One common misconception is thus that attackers target primarily 0-day vulnerabilities, leveraging the element of surprise to infiltrate systems. While zero-day exploits certainly garner attention due to their novelty and potential impact, the reality is that many attackers prefer to mix them with well-known vulnerabilities that have been around for a while, sometimes many years. These vulnerabilities persist due to various factors, including inadequate patch management, complex system dependencies, and the sheer volume of legacy software still in use.
It may also be worth repeating that an “attack” is often a combination of multiple tactics and techniques, sometimes lasting weeks or even months. Phishing may have been the vector used for gaining initial access, but it is usually followed by a patient discovery phase, often taking advantage of older vulnerabilities.
For example, we can see that Qualys reported that of the Top 20 Most Exploited Vulnerabilities in 2022 many are quite old, some dating back to 2012.
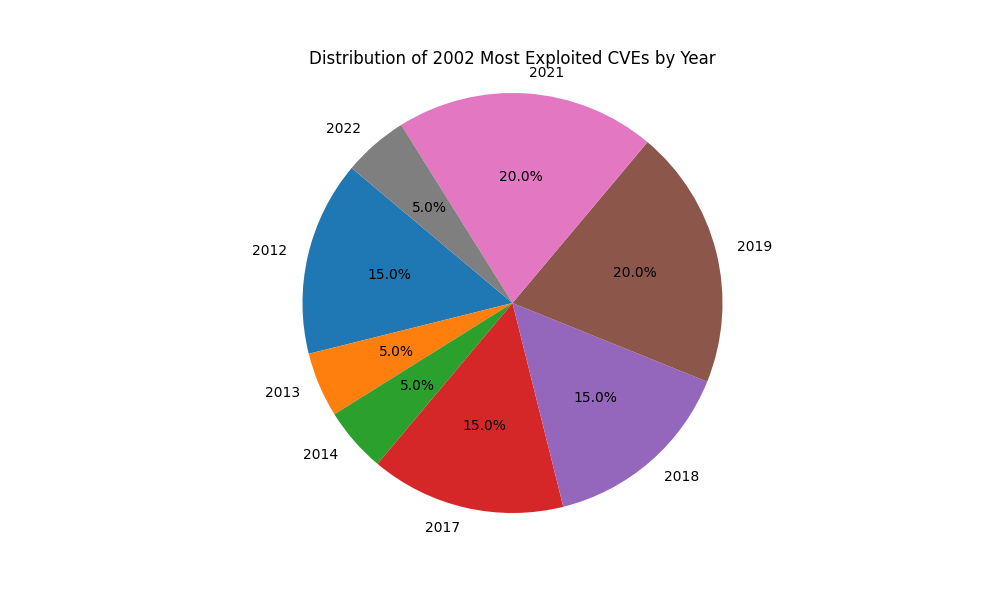
While other vendors may report different results according to their telemetry, they all include a mix of vulnerabilities found over the years. When you factor in common misconfigurations and the increased complexity due to the adoption of cloud computing, it should be clear that it has become almost impossible to guarantee that no unauthorized access will ever take place.
Zero Trust to the rescue
The above are some of the reasons why many organizations have adopted the Zero Trust security model. Zero Trust assumes that threats may exist both inside and outside the organization, and therefore strict access control and continuous monitoring are essential for security.
Deception Technology fits well into the model as it complements existing solutions, reduces detection time as well as alert fatigue, thanks to its very low false-positive rates. After all, with Deception Technology, the adversary only needs to be wrong once.
References:
- CISA Joint Security Advisory Top Routinely Exploited Vulnerabilities
- Qualys, Top 20 Most Exploited Vulnerabilities
- Okta, The State of Zero Trust Security 2023
Ready to try deception?
If you are interested in trialing Defused deception technologies and seeing just how easy it is to enhance your visibility into attacks then visit https://console.defusedcyber.com/signup/ and get started in less than 30 minutes.