When Patching Doesn't Help - CVE-2015-2291 (Bring Your Own Vulnerable Driver)

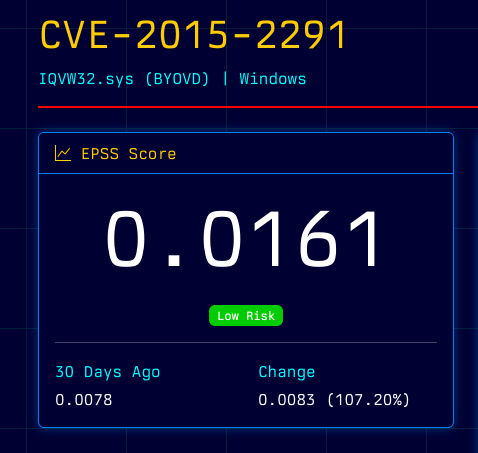
Something interesting caught our eye whilst running vulnerability data scrapes, namely looking at EPSS scores and which vulnerabilities have ballooned in exploit risk the most during the last month.
(For those who don’t know what EPSS is, it is an open initiative for predicting exploit likelihood of vulnerabilities. Read more at the EPSS home page.)
During the last 30 days, the #1 fastest grower in exploit risk was a 10-year old vulnerability, with it’s exploit risk haven spiked +107.20% in the last month.
This vulnerability (CVE-2015-2291) sits in the Intel Ethernet diagnostics driver (IQVW32.sys and IQVW64.sys) for Windows, allowing a local user to execute arbitrary code in kernel mode.
The EPSS score spike is presumedly happening because some recent attacks have used this old vulnerability. Attackers may introduce an old, vulnerable & signed driver to bypass Windows kernel protections (something called the “BYOVD” technique).
This is quite an interesting technique in that it allows attackers to reintroduce already patched vulnerabilities into environments (or introduce vulns that didn’t exist in the first place!)
The sections below cover where the driver is found, how attackers deploy it, the BYOVD method, real-world abuse, and some defensive measures.
The Vulnerable Component
As mentioned, CVE-2015-2291 sits in IQVW32.sys - which is a part of Intel’s Ethernet diagnostics tools. In normal circumstances, it is installed with various Intel network adapter software. Alternatively, some third party libraries, such as C-Docto also carry the driver with them. It is unlikely this is shipping legitimately in 2025 anymore, but you never know.
It is worth checking for the driver if you still have infrastructure running:
- Windows7, Windows 8, Windows8.1, Windows 10,
- Windows* Server 2008,
- Windows* Server 2008 R2,
- Windows* Server 2012,
- Windows* Server 2012 R2
Specifically, the versions affected by the vulnerability are in both iQVW32.SYS and iQVW64.SYS versions prior to v1.3.1.0.
A defender (or attacker for that matter) can check for the driver by enumerating installed or loaded drivers (e.g. using driverquery, WMI or Sysinternals tools) and looking for iqvw32.sys, iqvw64.sys or variants like iqvw64e.sys.
Worrying About the Supply Chain is Half of the Risk
Now we get to BYOVD, a.k.a. Bring Your Own Vulnerable Driver. If the vulnerable driver doesn’t exist, attackers can “bring” the vulnerable driver themselves onto the target system.
For example, in some observed attacks the adversary carried the outdated iqvw64.sys binary and replaced the on-system driver with their copy, effectively “rolling back” any patched version. Tools like PowerShell or direct Service Control commands can install the rogue driver.
Once loaded, the driver’s flaws can be exploited. (Notably, because the Intel driver is signed by Intel, Windows will load it under normal signature rules.)
Since it’s exploiting an old vulnerability, known exploit tools exist. These tools map drivers into kernel memory, bypassing Driver Signature Enforcement entirely. An attacker with administrator privileges can thus drop the vulnerable driver onto the machine and programmatically invoke the exploit to elevate privileges or load additional code.
It’s pretty crafty. Modern Windows enforces 64-bit drivers to be signed, but BYOVD detours this by using old signed drivers with known vulnerabilities. Once loaded, the attacker may get full SYSTEM privileges, can disable security software, install rootkits, etc., all under the guise of a trusted driver.
Recent Known Exploits by Threat Actors and Malware
Scattered Spider
The threat actor Scattered Spider were known to use the vulnerability in late 2022/early 2023. They attempted to load a malicious driver via CVE-2015-2291 in iQVW64.sys to bypass multiple EDRs. Scattered Spider’s driver was signed with stolen certificates and leveraged the vulnerability to deactivate security products (patching their drivers in memory.)
DOGE Big Balls Ransomware
In 2025, Netskope and Cyble reported a ransomware campaign where payload “ktool.exe” installs and exploits the vulnerable iQVW64.sys driver (CVE-2015-2291). The attacker used BYOVD to gain kernel access and after launched a Havoc Demon implant before encryption. Cyble explicitly notes: “use of a vulnerable Intel driver (CVE-2015-2291) in a BYOVD tactic” gave the attacker kernel-level access to disable logging and elevate privileges. This recent exploitation is likely driving the exploit likelihood score into frameworks like EPSS.
Other Malware
Naturally, BYOVD isn’t limited to this specific Intel driver. Trend Micro and others have documented ransomware (e.g. BlackByte, Cuba, LockBit) and nation-state groups (e.g. Lazarus) abusing vulnerable signed drivers (often renamed anti-cheat or utility drivers) to disable security measures.
A Few Mitigations and Detection Strategies
Patch or Remove the Driver
The primary defense is to eliminate the vulnerable driver. Intel’s update fixes CVE-2015-2291 in v1.3.1.0 (Connections CD 20.1+). Ensure all systems have the updated Intel Ethernet software. If the driver is not needed, uninstall Intel Network Connections/PROSet software, or manually remove iqvw32.sys/iqvw64*.sys from %SystemRoot%\System32\drivers and reboot.
Search / Hunt
Actively scan for iqvw32.sys/iqvw64e.sys on endpoints. Defender or SIEM tools can query loaded drivers or filesystem for these names. Log and alert on any unexpected loading of an Intel NIC diagnostics driver. YARA/Sigma rules (e.g. from the LOLDrivers project) can flag the specific driver binary or service creation. (For example, Sysmon’s ImageLoad or ServiceCreate events could detect loading of iqvw64e.sys.)
Driver Signing Policies
Enable Windows kernel driver signature enforcement (DSE) and hypervisor-protected code integrity (HVCI) wherever possible. Windows 11 (22H2+) has the Vulnerable Driver Blocklist enabled by default when HVCI (memory integrity) is on. When active, any driver on Microsoft’s blocklist is prevented from loading. On older Windows or if HVCI cannot be on, apply the blocklist manually: use Windows Defender Application Control (WDAC) or AppLocker to block known vulnerable drivers (Intel’s driver is on the list of vulnerable ones). Microsoft also provides a kernel-level ASR (Attack Surface Reduction) rule “Block abuse of exploited vulnerable signed drivers” which prevents adversaries from writing vulnerable driver files to disk (note: it doesn’t block already-present drivers from loading, but blocks new malicious drops).