Learnings From The Dispossessor Ransomware Leak

The malware repository VXUnderground recently released a large data leak from the ransomware group Dispossessor, containing a data dump of their support data repository for executing ransomware campaings - tools, manuals, procedure charts, credentials and so forth.
The Dispossessor ransomware group (also known as Radar) emerged in August 2023. Dispossessor targeted small to mid-sized businesses across various sectors, including manufacturing, education, healthcare, financial services, and transportation. Dispossessor used a dual-extortion model, where they infiltrated systems through vectors such as weak passwords, and after gaining initial access commenced to both encrypt data and exfiltrate sensitive information to apply extra pressure onto victims to encourage ransom payment. Their operations were global, affecting multiple dozens of companies in countries like the United States, Germany, and the United Kingdom.
In August 2024, a coordinated international law enforcement effort led by the FBI dismantled the group’s infrastructure, seizing multiple servers and domains, effectively disrupting their activities.
It is not clear who leaked their data, however it offers a rare insight into the “mind” of a ransomware operation.
In this blog post we will examine, analyze and speculate at this from a tools, techniques and procedures viewpoint.
Tools
The tools contains a lot of what has been seen in other campaigns. LSASS dumping tools like Mimikatz (and its friend Mimidogz), SharpLAPS for LAPS passwords, network scanning tools like NMAP & Advanced IP Scanner, various vuln exploit tools both including Metasploit but also specific exploit scripts for common vulns, AD scanners, RATs, and a big bunch of legitimate system optimization tools for encryption, cleanup, tunneling and so forth.
It does seem that out of the roughly 2000 files within the entire dump, there is almost a total absense of tools for any cloud-related attack vectors - apart from a single subscript in the PowerSharpPack tool - everything is purely for “on-premise” environments, almost totally geared towards Windows environments (a few Linux-based exploit scripts and helpers exist in the data dump, but these are very few in number.)
Included tools are as follows:
Credential Harvesting Tools
- Mimikatz: Extracts plaintext passwords, hashes, PIN codes, and Kerberos tickets from memory.
- Mimidogz: Similar to Mimikatz; used for credential dumping.
- Dumpert: Dumps LSASS memory to extract credentials while evading antivirus detection.
- Nanodump: Efficiently dumps LSASS memory for credential extraction.
- SharpSecDump: A C# tool for dumping credentials from the Security Account Manager (SAM).
- SharpLAPS: Retrieves local administrator passwords managed by Microsoft’s LAPS.
- WebBrowserPassView: Recovers passwords stored by web browsers.
- BRUTE Admin: Tool for brute-forcing administrator passwords.
- CME (CrackMapExec): Post-exploitation tool that includes credential dumping features.
- Rubeus: Kerberos ticket extraction and manipulation tool.
- PowerSharpPack: Post-exploitation toolkit using PowerShell scripts for credential dumping and other tasks.
Scanning Tools
- Nmap: Network scanning tool for discovering hosts and services.
- Netscan: Scans networks for connected devices and open ports.
- Advanced Port Scanner: Scans for open ports on network devices.
- SoftPerfect Network Scanner: IP, NetBIOS, and SNMP scanner.
- ShareFinder: Discovers shared resources on a network.
- SCANNERS: Collection of various scanning tools.
- Dnsdumpster: Performs DNS reconnaissance for a domain.
Exploitation Tools
- Metasploit Framework: Platform for developing and executing exploits.
- MS17-010_AutoBlue: Exploit for the EternalBlue vulnerability (MS17-010).
- NoPac: Exploits Active Directory vulnerabilities for privilege escalation.
- Zerologon: Exploit for CVE-2020-1472 allowing privilege escalation.
- Windows-Exploit-Suggester: Suggests potential exploits based on system vulnerabilities.
- EXP: General term for exploit tools.
- UniversalTermsrvPatch: Modifies terminal services for multiple RDP sessions.
- DFSCoerce: Exploits DFS referrals for privilege escalation.
- log4shell: Exploit or test for Log4j vulnerabilities (CVE-2021-44228).
Remote Access Tools
- AnyDesk: Remote desktop software for remote control.
- RADMIN: Remote administration tool.
- RdpChecker: Tests Remote Desktop Protocol connectivity.
- UltraVNC: Remote control software.
- PuTTY/KiTTY: SSH and Telnet clients for remote access.
Obfuscation Tools
- Invoke-Obfuscation: Obfuscates PowerShell scripts to evade detection.
- Spoofer.exe: Alters system identifiers to conceal identity.
- DLL: Could refer to tools involving DLL injection for code execution or persistence.
Tunneling and Proxy Tools
- NGROK: Creates secure tunnels to localhost, exposing local servers.
- Proxifier: Redirects network connections through proxy servers.
- SOCKS: SOCKS proxy utilities for network traffic tunneling.
- TOR: Enables anonymous communication over the internet.
Reconnaissance and Enumeration Tools
- AdFind: Queries Active Directory information.
- SharpHound: Collects data for analysis with BloodHound to map Active Directory relationships.
- FishEye: If referring to Atlassian’s tool, used for browsing code repositories.
- SharpHound: Collects data for BloodHound to map Active Directory relationships.
- FindSPN: Retrieves Service Principal Names for Kerberos attacks.
- IMPACKET: A collection of Python classes for working with network protocols (e.g., SMB, NTLM, Kerberos).
- Certipy: Tool for abusing Active Directory Certificate Services.
- LLMNR Protocol: Utilized for local network reconnaissance and exploitation.
System Utilities and Development Tools
- Python Portable: Portable version of the Python programming language.
- Python Installer: Installs Python environment.
- PyCrypto: Cryptography library for Python.
- SCRIPTS/SCRIPTS_elcin: Custom scripts for various automation tasks.
- WinRAR: File archiving utility.
- Total Commander: File management software.
- CCleaner: System optimization and cleaning tool.
- WinPcap/Win10Pcap/Npcap: Packet capture libraries for network traffic analysis.
- OpenGLChecker.exe: Checks system’s OpenGL capabilities.
Data Exfiltration and Synchronization Tools
- RCLONE: Syncs files to and from cloud storage services.
- Syncthing: Continuous file synchronization between devices.
- GRAB: Collects data from target systems (potentially for exfiltration).
- FTP download by target: Tool for targeted file downloads via FTP.
Network Utilities
- PING: Tests network reachability of hosts.
- WinPcap/Win10Pcap/Npcap: Libraries for capturing network traffic.
- SMBmap: Assesses and exploits SMB shares across networks.
Password Recovery and Brute-Forcing Tools
- WebBrowserPassView: Recovers saved web browser passwords.
- BRUTE Admin: Performs brute-force attacks on administrator accounts.
VPN and Remote Connectivity Tools
- FortiClient: Security suite with VPN capabilities.
- NetExtender: VPN client for secure remote access.
- OpenVPN/OpenVPN Portable: VPN clients for secure network connections.
Data Discovery Tools
- SauronEye: Searches for files containing specific keywords.
Anonymity and Identity Concealment Tools
- TOR: Provides anonymous communication over the internet.
- Spoofer.exe: Spoofs network identifiers to mask identity.
Web Browsers
- Chrome: Web browser by Google.
- Firefox: Web browser by Mozilla.
File Synchronization Tools
- Syncthing: Synchronizes files across devices.
- RCLONE: Syncs files with cloud storage.
Packet Capture and Network Analysis Tools
- Npcap: Packet capture library.
- WinPcap/Win10Pcap: Network packet capture utilities.
Tactics, Techniques and Procedures
Following from the above, techniques are very focused on executing the full required “attack chain” after gaining access into a Windows environment.
The leak folders hundreds of different supporting manuals and readmes for conducting attacks. For instance, the total amount of .txt and .md (markdown) files amounts to over 500.
A lot of information between these manuals is overlapping. Selecting one file for examination, a cohesive “First Steps Manual”, contains a 101 on Active Directory Environment (including basic terminology) and hand-holds would-be actors on how to go about conducting their ransomware campaign in an end-to-end fashion. Below are multiple excerpts (translated from Russian into English) from a file called “First Steps Manual”:
Steps for Gaining Access:
0. Preparation on Dedicated Server:
Disable Windows Defender.
Load all necessary software.
Install .NET Framework 3.5 if you have Windows 10. When executing commands, it may suggest installing it automatically.
For Windows Server 2016: Install .NET Framework 3.5 through Server Manager.
For Windows Server 2019 or later: You'll need to download the image.
....
1. Network Reconnaissance:
Open the console on your dedicated server.
Run the command:
ipconfig /all
....
2. Obtain FQDN of the Domain Controller:
Since DNS = Domain Controller in corporate networks, use the DNS IP addresses.
For each DNS IP address, run:
ping -a <DNS_IP_Address>
The output will provide the FQDN of the Domain Controller (DC).
....
3. Extracting AD Information with AdFind:
Substitute your values as previously described.
Using AdFind to Extract AD Info through VPN
Open cmd and run:
ipconfig /all
Locate the VPN interface and note the DNS server; this is your DC (there may be multiple).
....
4. Sorting AD Computers:
On your Linux machine, place the script script_sort_ad_computers.sh in the folder containing the AdFind output.
Open a terminal in that folder and run:
chmod +x script_sort_ad_computers.sh
./script_sort_ad_computers.sh
The script will sort the data, creating files like SERVERS, WORKERS, etc...
....
With the FQDNs and IP addresses of your domain controllers, attempt the following vulnerabilities in order.
1. CVE-2020-1472 - Zerologon (Using Mimikatz):
....
More domain specific manuals:
AV Disabling
AV disabling manuals exist for killing endpoint detection / protection agents for at least Sophos, Windows Defender, Trend Micro and Bitdefender.
Despite the basic manuals focusing on the above vendors, broader resources exist for killing other vendors too- batch scripts for eliminating AV presence on both local, service level as well as network level, a file with over 1000 AV process names listed, presumedly for identifying running AV agents on endpoints, and so forth.
It’s also noteworthy that much like the Ransomhub actors, a manual exists describing the use of Kaspersky Labs’ TDSSSKiller (originally designed to be a rootkit remover) to eliminate the above mentioned agents off of endpoints.
Backup handling
Specific techniques are described to abuse backup servers. For example, a manual exists describing a method for accessing server backups managed by ShadowProtect SPX by first obtaining RDP access to a server, using the SPX software to identify backup locations, and then extracting or cracking credentials through techniques like hash dumping or using tools such as Mimikatz. A similar manual is present for Synology systems.
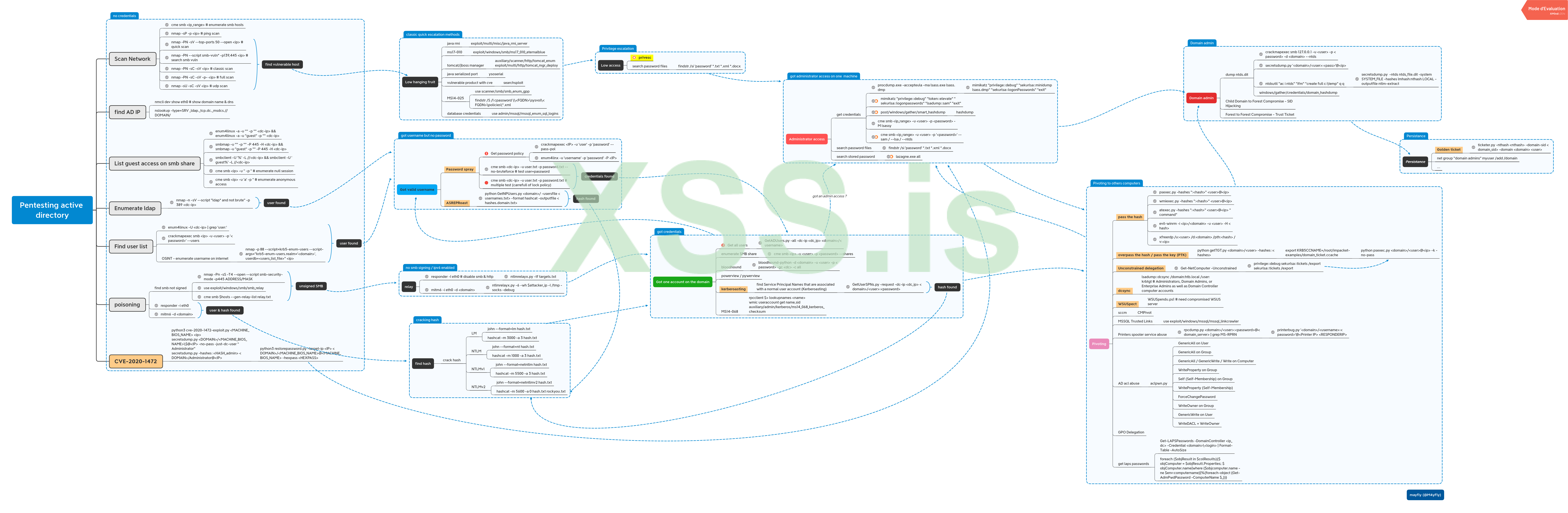
Active Directory Abuse
Flow charts (borrowed from elsewhere, as evident) have been included for the benefit of the attackers:
Infrastructure
Multiple of the IOCs included, like IP addresses used to host C2 infrastructure, remain almost fully clean according to VT. CriminalIP seems to be doing a good job as it is in many cases the only vendor to highlight malicious IP addresses / URLs embedded in the leak (we have no affiliation to them.)
C4 frameworks used include Brute Ratel, including a seemingly official tutorial video of its use stashed into the C2 subfolder.
Encryption
The ransomware subfolders contain executables for the Babyk ransomware. Outside of Windows environments, Babuk is also designed to target VMware ESXi servers. Multiple manuals inside the leak repo discuss operating procedures for handling ESXi encryption as efficiently as possible; for instance, it is noted HA (high availability) should be disabled, among other things:
The way to do it is just disable HA on vcenters, we do it via script, then just encrypt all esxis except the foothold(GATEWAY, IP , etc), then encrypt that one last in the very end. if you don't disable HA as soon as you shutdown VMs , vcenter will move it to another esxi and turn it back on.