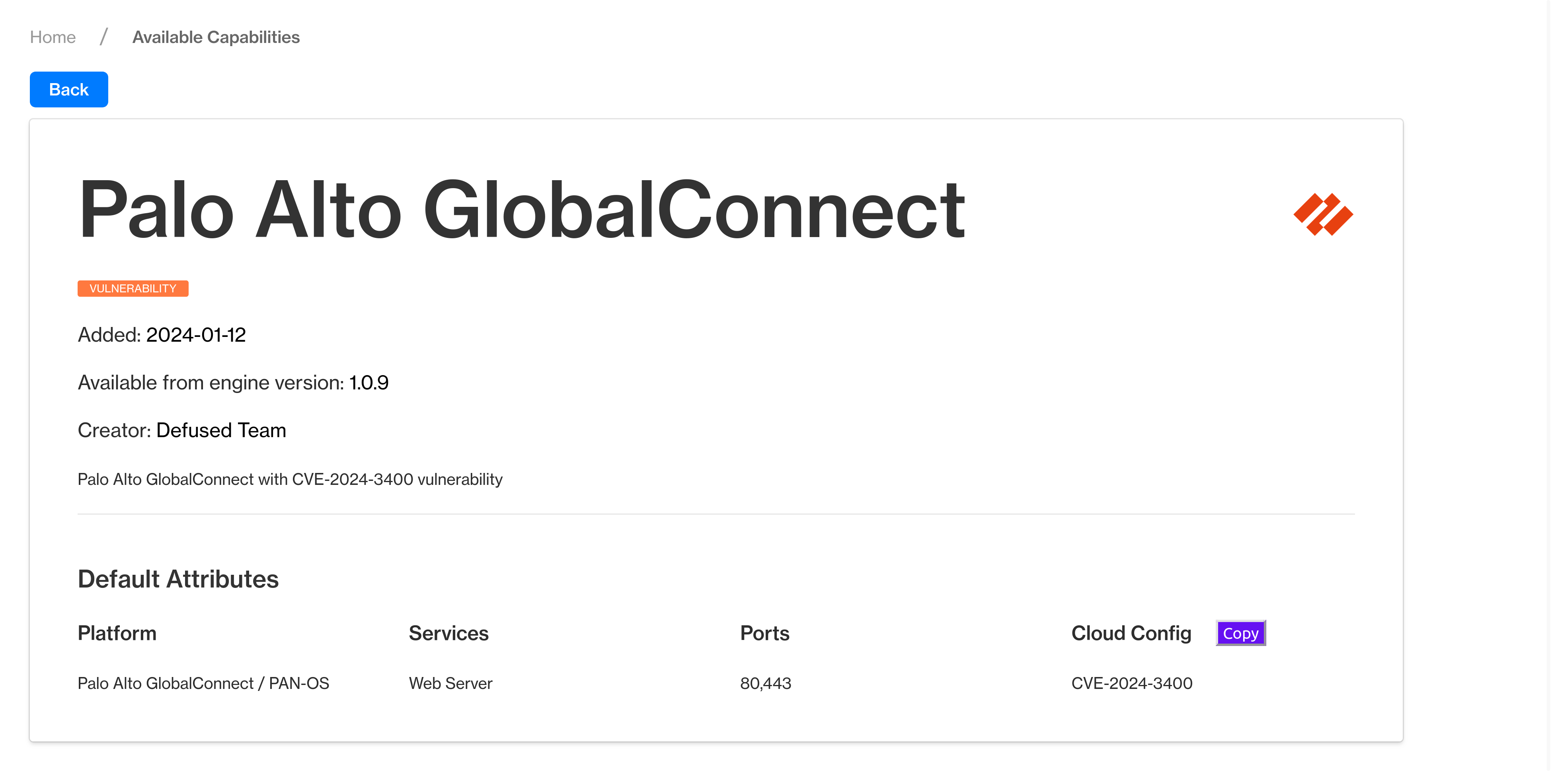
Internal Breach Detection
Discover and mitigate breach blast radius with simple to deploy internal deception components.
Deploy Now for Free
Key Benefits
Protect Crown Jewels
Detect, defuse and build threat intel of attack against your crown jewels like ERP systems, virtualization infrastructure, manufacturing assets and more.
Close Visibility Gaps
Replicate bespoke internal assets to build detection and response-like capabilities for your application attack surface
Increased Detection Maturity
Features like the attacker sandbox build high-granularity internal threat intelligence for analyzing and closing incidents faster
Ready to get started?
Start Now for Free